This research was conducted to measure the safety of heat stable enterotoxin a (STa) produced by enterotoxigenic Escherichia coli, through studying its toxic effect on human blood lymphocyte, since it showed a promising effect in reducing the proliferation of colorectal cancer cells. the cytogenetic effects of (STa) by using five different concentrations (100, 200, 400, 800 and 1600μg/ml) in comparison with negative (PBS, Phosphate buffer saline) and positive (MMC, Mitomycin C) at concentration of 5μg/ml, controls on human blood lymphocytes obtained from both (10) normal healthy persons and (20) colorectal cancer patients was measured by employing the following parameters: mitotic index, blast index, chromosomal aberrations and micronucle
... Show MoreBackground: The PMMA polymer denture base materials are low in thermal and strength properties. The aim of the study was to investigate the change in glass transition temperature, E-Moudulus and coefficient of thermal expansion of acrylic denture base material by addition of Al2O3, TiO2 and SiO2nano-fillers in 5% by weight. Materials and methods: The type of polymerization is free radical bulk polymerization. one hundred twenty (120) specimens were prepared , the specimens were divided into four groups according to the material had been added (one control and three for Al2O3, TiO2 and SiO2nanocomposite) each group was subdivided in to three groups according to the test had been done on it, the degree of transition (Tg) was measured by The d
... Show MoreSoftware Defined Network (SDN) is a new technology that separate the control plane from the data plane. SDN provides a choice in automation and programmability faster than traditional network. It supports the Quality of Service (QoS) for video surveillance application. One of most significant issues in video surveillance is how to find the best path for routing the packets between the source (IP cameras) and destination (monitoring center). The video surveillance system requires fast transmission and reliable delivery and high QoS. To improve the QoS and to achieve the optimal path, the SDN architecture is used in this paper. In addition, different routing algorithms are used with different steps. First, we eva
... Show More (6)
(6)
 (3)
(3)
This paper presents thermal characteristics analysis of a modified Closed Wet Cooling Tower (CWCT) based on heat and mass transfer principles to improve the performance of this tower in Iraq. A prototype of CWCT optimized by added packing was designed, manufactured and tested for cooling capacity of 9 kW. Experiments are conducted to explore the effects of various operational and conformational parameters on the thermal performance. In the test section, spray water temperature and both dry bulb temperature and relative humidity of the air measured at intermediate points of the heat exchanger and packing. Heat exchangers consist of four rows and eight columns for an inline tubes arrangement and six rows and five columns f
... Show MoreThe research aims to find ways to minimize the use of quantities of chemical fertilizers in agriculture in order to get to an environment that is free of contaminants. Magnetized water technology used in the experience of planting seeds of tomatoes Thomson type to obtain a higher efficiency to absorb fertilizer NRK in the protected environment of the period from February to June. Magnetized water system used locally made levels Gaues (4800,2500,1500) concentrations of 50 to 100% for each level and the rate of (4) replicates, and results indicated that the severity of the magnet (4800 Gaues) and a concentration of 50% gave the highest percentage of tomato fruit size and intensity ( 1500 Gaues) and a concentration of 100% did not give any inc
... Show More (1)
(1)
Water pollution is an issue that can be exacerbated by drought as increased concentrations of unwanted substances are a consequence of lower water levels. Polluted water that flows into natural marshlands leads to the deposition of pollutants in the interior of the marsh. Here we present evidence that the interior of the Central Marsh (CM) in southern Iraq suffers from higher levels of pollution than areas closer to the source of water entering the marsh (the Euphrates River). A 1.7m embankment that halts the flow of the Euphrates is only infrequently breached and so the CM is effectively the terminal destination of the waters (and their associated pollutants and agricultural waste) flowing from the West of Iraq.
A range of water
... Show More (9)
(9)
 (3)
(3)
The steady 3-D raw water turbulent flow is numerically investigated. This flow is formed of solid silica sand (quartz) carried by water in stainless steel pipe. The flow in a straight pipe and flow in a pipe with a sudden contraction are analyzed using a two-way coupled Eulerian-Lagrangian approach. Erosion rate is estimated by Oka erosion model combined with the constant coefficient of restitution. The effect of solid particles mass flow rate, inlet velocity, particle diameter, internal pipe diameter, orientation, contraction coefficient, and wall pipe contraction angle on erosion rate are examined. The predicted erosion is distributed homogenously for straight pipe, while the step wall area of the contraction is the most eroded part. The
... Show More (2)
(2)
 (1)
(1)
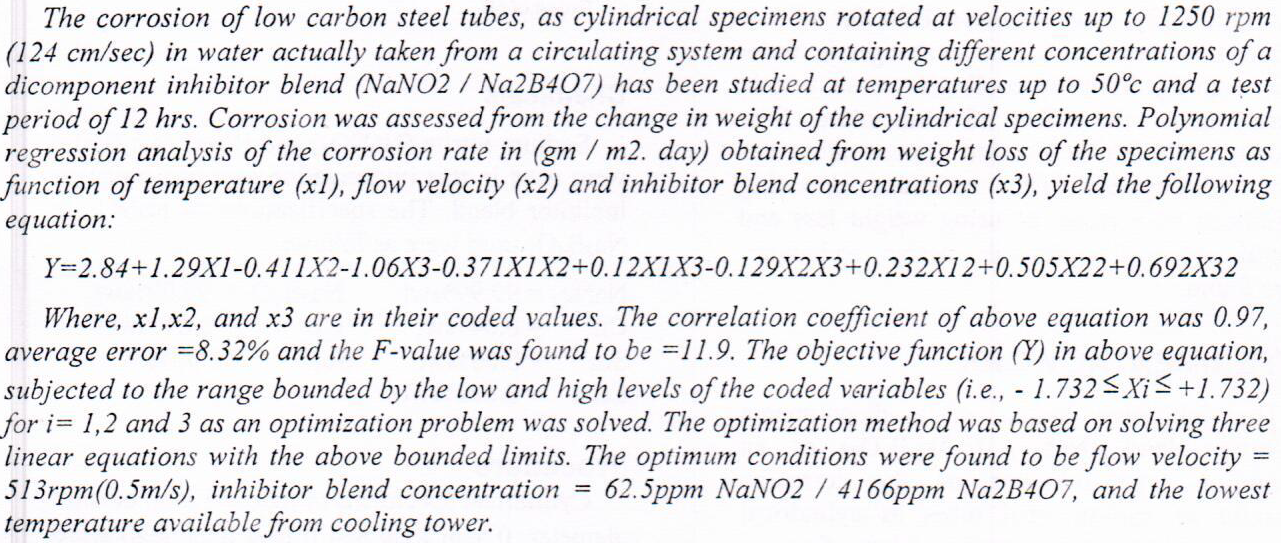
The inhibition of mild steel corrosion in 1.0M HCl by 1-propanol and the synergistic effect of potassium iodide (KI) was investigated using weight loss and polarization techniques in the temperature range (30 ‒ 50) ̊ C. A matrix of Doelhert to three factors was used as the experimental design, adopting weight loss results as it permits the use of the response surface methodology which exploited in determination of the synergistic effect as inhibition on the mild steel. The results were confirmed using electrochemical polarization measurements. Experimental results showed that the inhibition efficiency (IE%) increases with increase in concentration of inhibitor and with increasing of temperature. The addition iodide ions t
... Show MoreStenography is the art of hiding the very presence of communication by embedding secret message into innocuous looking cover document, such as digital image, videos, sound files, and other computer files that contain perceptually irrelevant or redundant information as covers or carriers to hide secret messages.
In this paper, a new Least Significant Bit (LSB) nonsequential embedding technique in wave audio files is introduced. To support the immunity of proposed hiding system, and in order to recover some weak aspect inherent with the pure implementation of stego-systems, some auxiliary processes were suggested and investigated including the use of hidden text jumping process and stream ciphering algorithm. Besides, the suggested
... Show More